WordPress, like any software, has flaws that hackers may exploit. In this essay, I would like to share some of my personal experiences with WordPress security risks so that you can avoid making the same errors I did.
This post will go over some common types of vulnerabilities and what you can do to help keep your WordPress installation safe. Any website, no matter how little or small, is vulnerable. Hackers might exploit even the tiniest one to scam visitors.
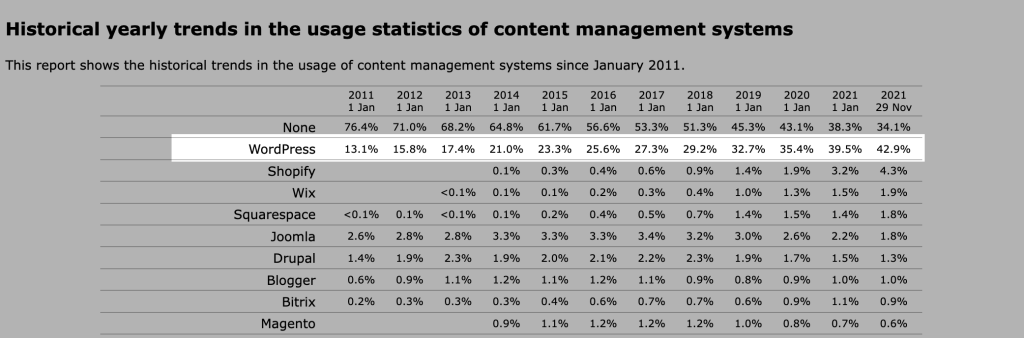
WordPress is the content management system of choice for 65.1% of the websites tracked by W3Techs. This represents 42.9% of all webpages. Furthermore, 20.3% of all WordPress-powered websites utilize WooCommerce. This figure is continually growing; in 2011, just 13.1% of websites used WordPress; in the following ten years, it more than tripled.
In several places throughout the text, I have included figures from a study produced by Sucuri, one of the major firms specialized in offering website security solutions. If you are interested in reviewing the whole study, please visit this link to download the report as a PDF file.
What are the most common WordPress security vulnerabilities?
WordPress plugin and theme security risks
WordPress hacking using automated tools is the most common method since it is the most convenient and simplest method for hackers. They attempt to attack vulnerabilities in popular plugins and look for websites that use vulnerable plugins. In general, the danger is posed not by WordPress itself, but by the third-party plugins.
This does not imply that the WordPress codebase is completely secure. Because there are thousands of volunteers and engineers working on the codeebase, most faults and problems are quickly fixed. In 2021, just seven vulnerabilities were disclosed, according to CVE Details.
WordPress is open source, which means that anybody may write and publish a WordPress plugin or theme. However, in the vast majority of situations, no one does a thorough code examination before it is released into the public. The situation is not as bad if the plugin creator finds and patches the flaw, but when the project is abandoned, the security risk becomes significant.
One of the most common "sins" of website owners is failing to update software, which may make hackers' jobs much easier. According to Sucuri, at the time of infection, 49% of WordPress installations in 2019 were outdated.
Every now and again, a vulnerability in one of the most widely used plugins makes the rounds on social media. In September 2021, for example, WordFence staff discovered a backdoor in the OptinMonster plugin, which was installed on over a million websites. The holes in the plugin enabled any site visitor to export sensitive data and inject malicious JavaScript into the code.
Keep your plugins and themes up to date
To begin, you should update WordPress core, as well as plugins and themes, on a regular basis to keep your website safe. In addition, you may want to have a look at all the plugins you have already got set up on your WordPress website. Less is more, and you should constantly get rid of the ones you do not need. Even if the plugin is not turned on, its backdoors may be exploited to take over your website. If the plugin was not updated for months and its developer no longer maintain it, you should replace it with a more dependable alternative.
Avoid "nulled" plugins and themes from GPL marketplaces
In addition to this, you should avoid downloading plugins and themes from untrustworthy sites. Limit yourself to the WordPress.org repository or well-known companies with a large userbase. Attempting to get "nulled" plugins/themes from GPL marketplaces might result in security problems.
Spam security risk (comments and contact forms)
On compromised websites, spam infections were the most often identified security vulnerability. Unfortunately, you will have to deal with spam regardless of whether you allow comments or provide a contact form on your website. Most comment spam is automated, produced by spam bots using short, generic phrases to hide links. Often, the links will go to a website that contains malware or trick your visitors. Another issue that may arise here is that excessive comment spam may have a negative impact on your search engine results.
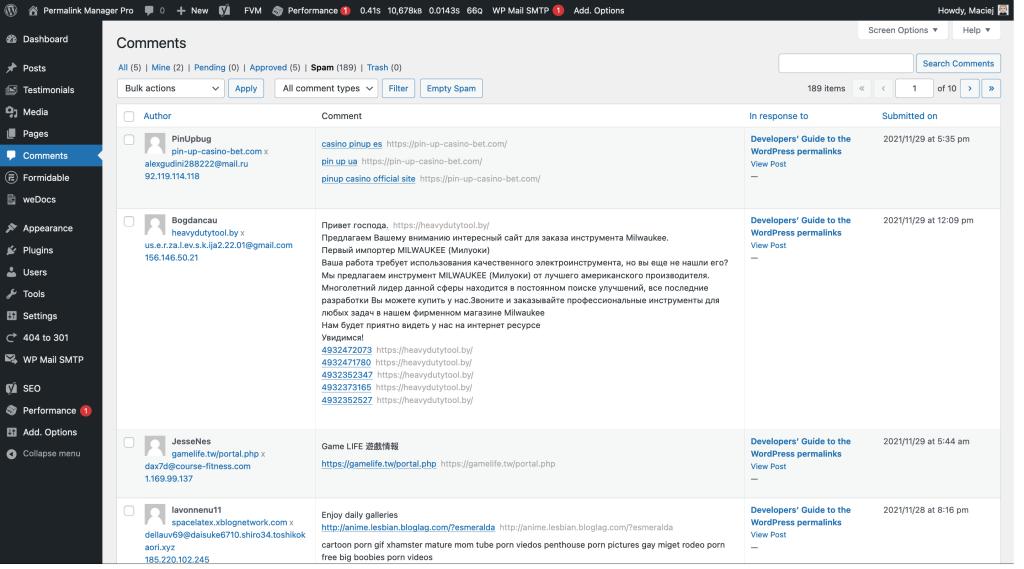
How to prevent spam security risks using WordPress built-in tools?
WordPress comes with a number of handy features that you may customize to fit your needs and prevent spam comments. To access them, go to the "Settings -> Discussion" area.
If you believe that this is insufficient, there are several third-party plugins available that will give extra spam protection. Akismet, the most popular, is pre-installed on WordPress sites and is free to use for personal bloggers. The plugin validates your comments and contact form entries against a global spam database.
How can you keep spam out of your WordPress contact forms?
Securing contact forms may be more challenging than securing the WordPress comment system. However, the majority of popular plugins contain significant features that may limit the quantity of spam submitted via forms. This allows you to simply implement one of the most used anti-spam solutions. The most frequent approaches are an Akismet integration module, reCAPTCHA, or a custom "honeypot" field.
To save you time, I have collected a list of instructions for the most popular contact form plugins.
If you use the Internet often, you have almost certainly come across reCAPTCHA. Because the concept is straightforward, I will not go over it in detail here and instead focus on a less apparent solution, the "honeypot" field.
How can a "honeypot" field help your contact form prevent spam entries?
The "honeypot" field concept is based on the fact that it is visible to spambots but not to actual human visitors. Even if the fields are not accessible to a real user, these spambots populate them with spam. Submissions with this field completed will be rejected since your form understands that this is the honeypot.
Compromised & weak passwords and brute force attacks
The safety of your users' personal data is crucial, especially in the wake of the GDPR, when the issue of data protection has reached a new level. To get access to your website, hackers may resort to brute-force attacks. In a nutshell, they use automated scripts with a vast number of text combinations to exploit weak passwords. Once this is accomplished and the hacker obtains administrator rights, the attacker has total control of the website.
Use strong passwords
Using difficult-to-guess passwords is a great first step in making your WordPress more secure. According to a recent National Cyber Security Centre research, the most often used password compromised to access critical information was '123456.'
Strong and complicated passwords are hard to remember, but also more difficult to break. The same goes for user names, which should be kept in mind along with passwords. Because early versions of WordPress defaulted to the login 'admin,' the bulk of assaults presume users are still using it. When you install a new website, choose a username other than the default 'admin'.
There are other ways to get access to your site that are not based on brute force, such as phishing. While trust is crucial, it is impossible to know where your login credentials will end up if you give them to a stranger. If you engage WordPress developers for freelancing work, you should not provide anybody access to your WordPress admin account unless absolutely necessary.
Limit login attempts
Limiting login attempts using the WP Limit Login Attempts plugin is another powerful defense. It is also a good idea to make access to your site even more difficult by changing your default admin URL. Using the WPS Hide Login plugin is the simplest method to do this.
How to protect your website from WordPress security risks?
I have previously mentioned some of the tips that will help you secure vulnerabilities on your WordPress site. Later in this post, I will go through some other options for making your site even more secure.
Can backup help to minimize WordPress security risks?
If you operate an internet-based company, you cannot afford to be offline even for a day, let alone lose all of your data. Having a backup might save your life for a variety of reasons, not only in the event of a hacker attack. For example, I was directly impacted by an infamous accident in March 2021, when the OVH Datacenter in France was destroyed by fire. Fortunately, I had a complete backup of this website, so I was able to restore all of the content in a matter of hours.
To put it another way, a backup is a copy of your website that can be quickly restored to service if anything goes wrong with your server. Whatever happens, keeping regular backups of your WordPress site may save you a lot of time and trouble.
If you are still reluctant to pay for an automated backup, consider how much time and money it would take to reconstruct everything from start if a hacker deleted files or database entries. Restoring a website from an automatic backup usually takes only a few minutes. You will still need to address the security flaws that the attacker used to breach your site, but at the very least, your site will be usable again.
In general, you should avoid keeping backup files on the same server as your live website. If anything goes wrong with your website, the backup files may be lost as well. Because of this, it is a good idea to have many backup options, including an external one (eg. "cloud"). As a result, if one backup server fails, you may still get your data from another source. Many hosting companies provide automatic backup as a service. Kinsta is a good example of this. Your data is safeguarded in the event of a catastrophe thanks to their redundant backup technology.

WordPress security plugins
One of the best ways to keep your WordPress site protected is to use a firewall. There are several types of firewalls available for safeguarding a website and security plugins are a popular option for WordPress users. There are a handful that provide limited functionality for free, but most worthwhile ones have a price tag. There are several WordPress security plugins accessible online, with the majority of the most popular options being all-in-one solutions. Listed in the table below are the three most popular WordPress security plugins.
| Name | Price | Free version |
|---|---|---|
| Wordfence | from 99 USD per year | Available |
| iThemes Security | from 48 USD per year | Available |
| Sucuri Security | from 200 USD per year | Available |
The ease of use is undoubtedly one of the most significant benefits of such a solution. With a plugin-based firewall, you can configure it yourself rather than hiring a professional. You can easily adjust or deactivate the plugin from your WordPress admin dashboard since it is installed on your server.
Unfortunately, this solution has several important downsides. To begin with, WordPress lacks a built-in mechanism to mitigate DDoS attacks. Due to the nature of DDoS assaults, plugin-based firewalls are essentially worthless. In this scenario, a network-based firewall is more effective since it can filter harmful traffic before it reaches your server. Because the plugin firewall is located on your server, it consumes a significant amount of resources and slows down the site.
7g .htaccess firewall
An Apache-powered server may be protected with a strong and completely free solution. Specifically, I use it on many of my sites to handle the most frequent WordPress security threats. The 7G Firewall provides lightweight, server-level security against a broad variety of malicious requests, bad bots, automated attacks and spam. One of the key advantages of this approach is that it is faster and uses less resources on the server than plugins or other PHP scripts.
The 7G Firewall is a sophisticated, well-optimized set of rewrite rules that validates all URI requests against a set of Apache or NGINX directives. This is done at the server level, which is good for speed since it reduces the need to load PHP and MySQL simply to reject a faulty request.
There is also a free WordPress plugin available if you do not know how to install it on your host.
Great insights on the biggest WordPress security risks! It's crucial to regularly update plugins and themes to avoid vulnerabilities. Implementing strong passwords and two-factor authentication can also make a huge difference in protecting your site. Staying proactive about security is key to maintaining a safe WordPress environment. Thanks for highlighting these important points!